- How to create site to site VPN for SMB with low IT budget. part1
- How to setup OpenVPN server on debian? part2
- How to create site to site vpn from pfsense to openvpn server.part3
OK, we already have Openvpn server at central office. Now our task is to configure branch office pfsenses (why pfsense) to connect central office Openvpn server:
- create Hyperv VM for pfsense at branch office 01:
- mount pfsense iso to the pfsense VM
- create fixed size virtual disk, 5gb is enough. if you use dynamic disk – pfsense freebsd installer can fail
- before pfsense installation add second vNIC
- connect both vNICs to the same vswitch (based on one physical NIC) !
- install pfsense on the VM
- during first booting choose en1 for WAN and en2 for LAN.
- Let’s consider that branch01 has 192.168.0.1 on tplink/dlink/Univsion-smartbox and so on router. Therefore assign 192.168.0.2 to WAN of pfsense and 172.16.101.1 to LAN interface.
- access to 172.16.101.1 from browser (before assign your workstation for example 172.16.101.100 ). Default credentials for pfsense is admin/pfsense.
- copy content of ca.crt and ca.key from Debian openvpn server to pfsense (i recommend – instead of ftp/winscp and so on, just from putty/ssh “cat ca.key” and by mouse select/copy content from screen – now just paste it into browser)
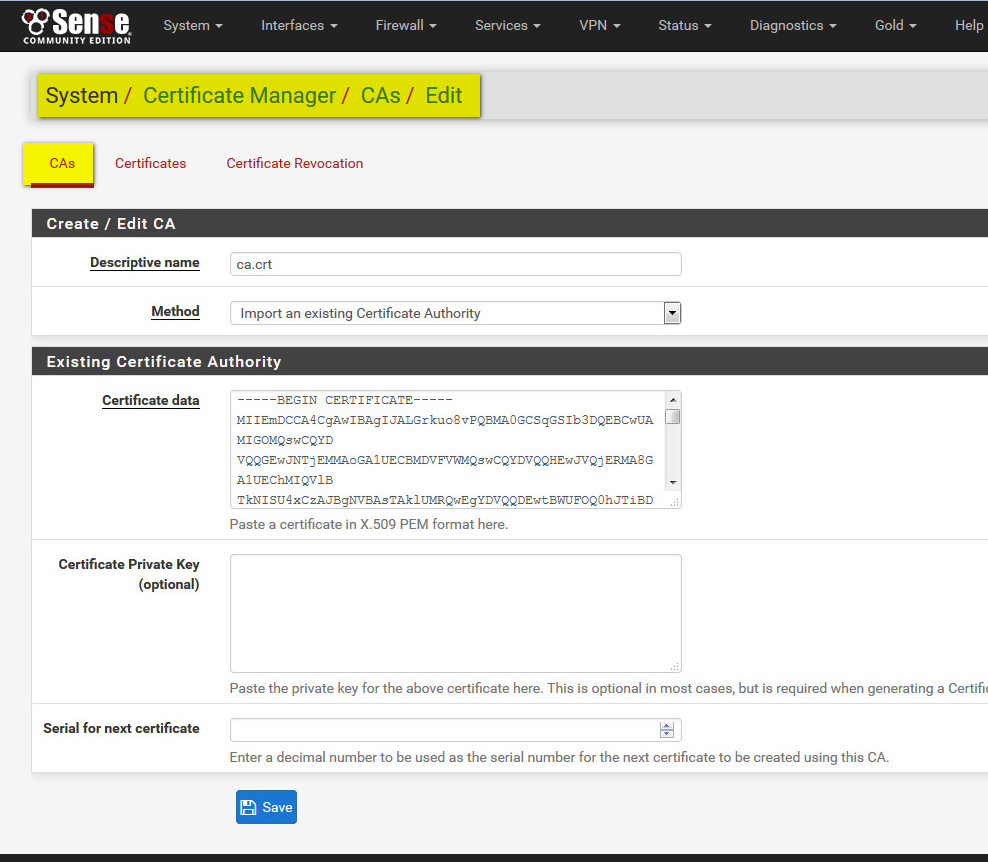
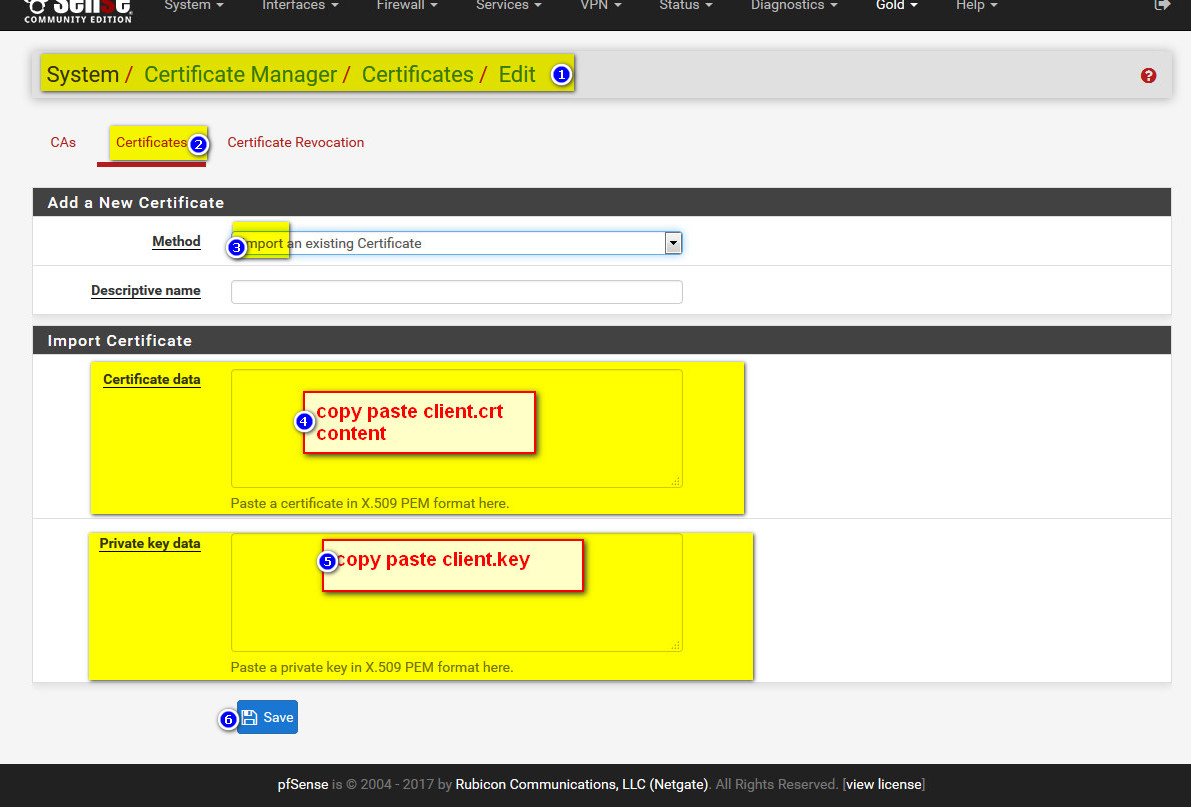
- add into pfsense client01.key and client01.crt
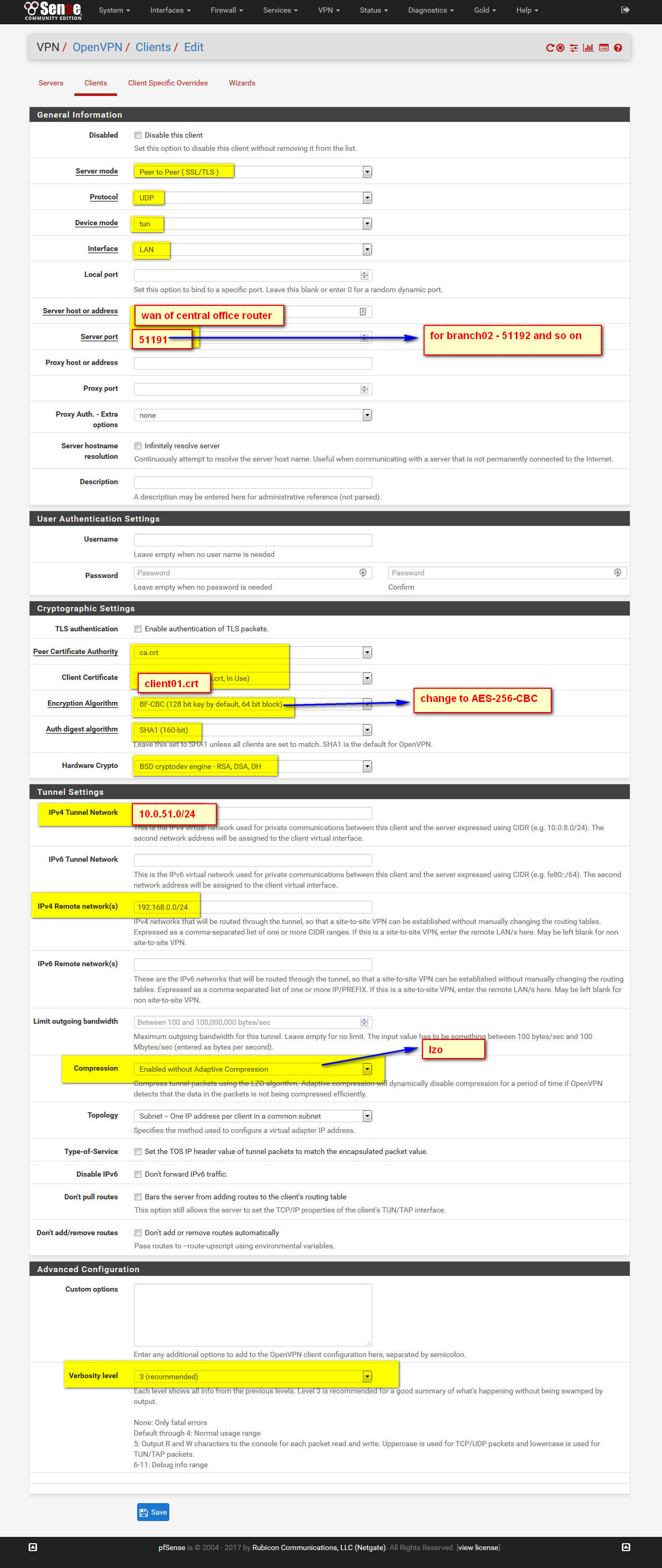
- configure openvpn client:
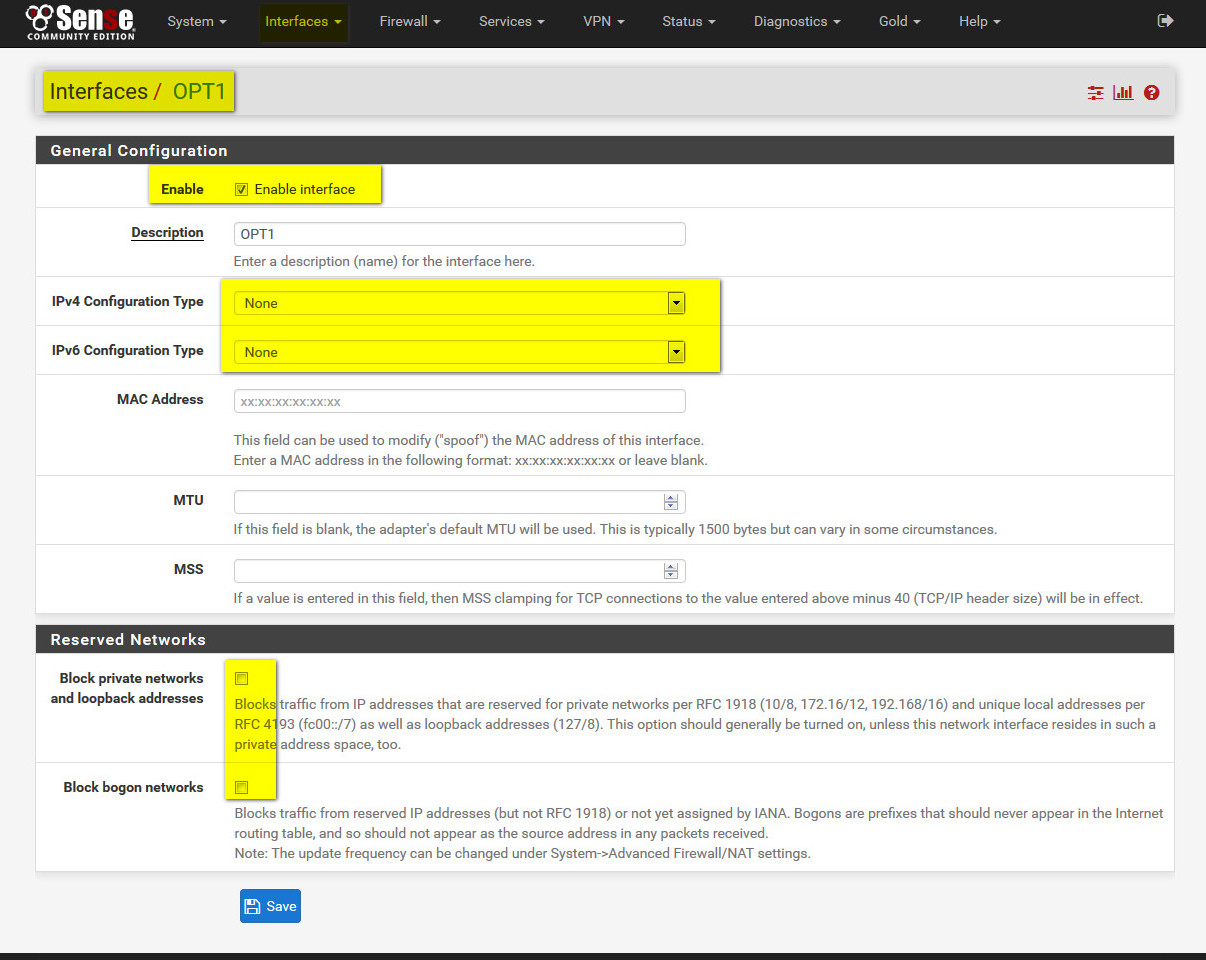
- enable optional interface:
- allow any traffic thru new OPT1 interface:
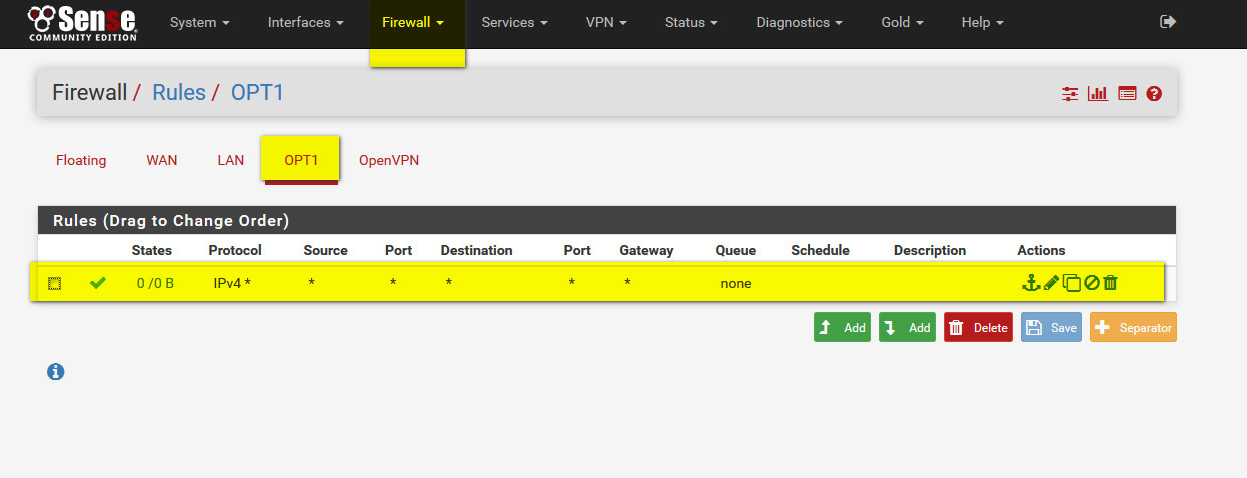
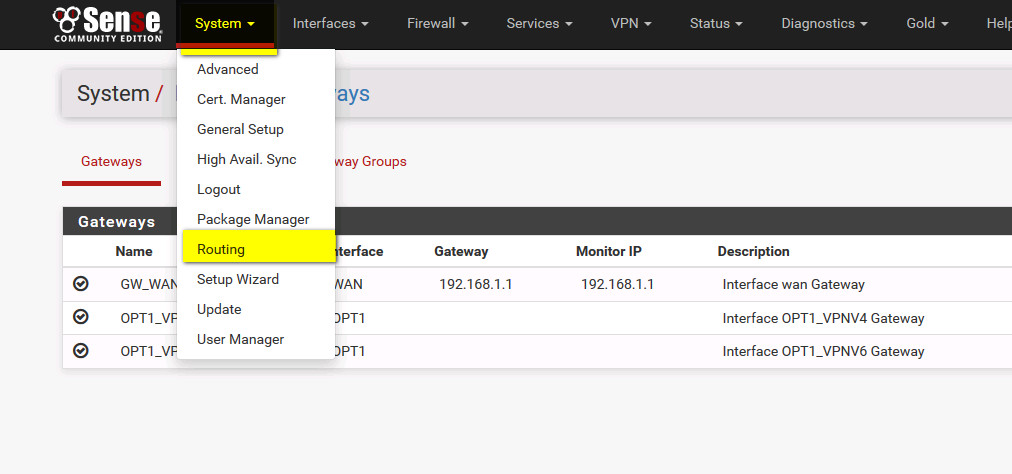
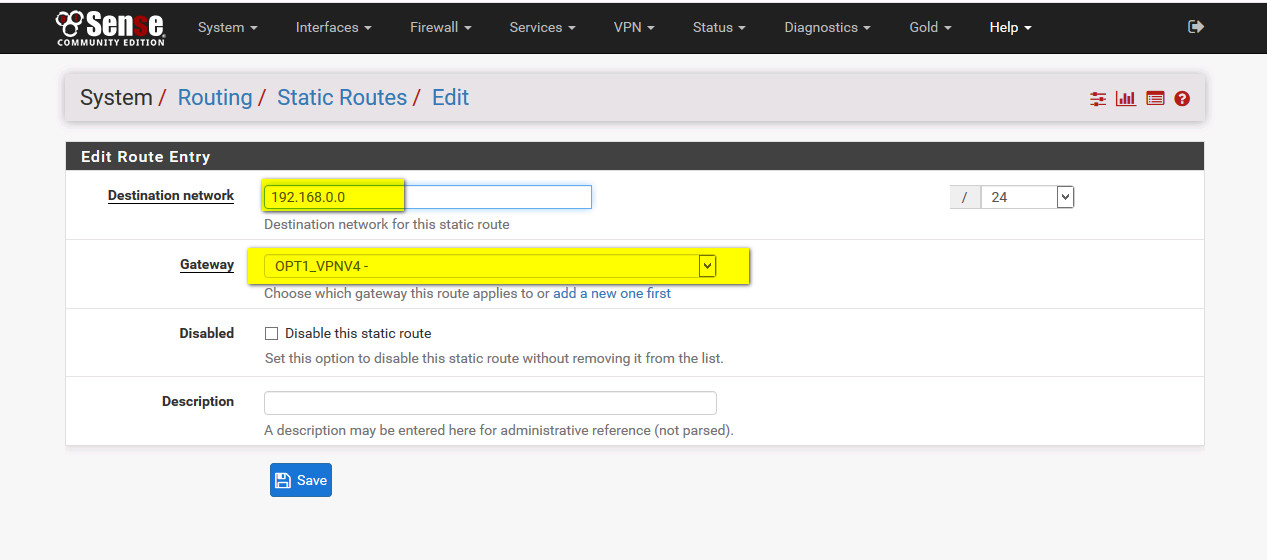
- create routing to central office :
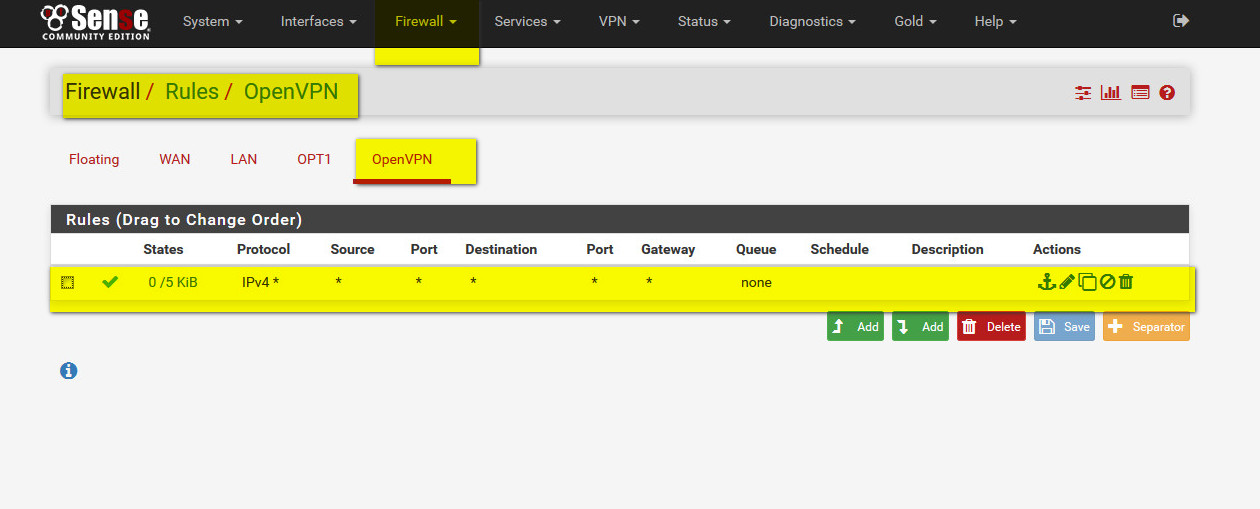
- to check state of vpn see from:
- above pfsense configuration more or less equals to openvpn client conf file:
client remote central.office.mn dev tun01 ifconfig 10.0.51.2 10.0.51.1 route 192.168.0.0 255.255.255.0 tls-client ca /etc/openvpn/easy-rsa/keys/ca.crt cert /etc/openvpn/easy-rsa/keys/client01.crt key /etc/openvpn/easy-rsa/keys/client01.key reneg-sec 60 verb 5 status /var/log/openvpn.log #log-append /var/log/openvpn01 port 51191 proto udp keepalive 10 120 comp-lzo cipher AES-256-CBC persist-key persist-tun
- Result: each branch office device with configured dgw (for example 172.16.101.1) will ping central office subnet and vice versa